- Watermarking and Steganography
- Signal Processing and Cryptography
- Multimedia Forensics
- Communications and Network Security
- Biometrics
- Applications

- Read more about Efficient Capon-based approach exploiting temporal windowing for electric network frequency estimation
- Log in to post comments
Electric Network Frequency (ENF) fluctuations constitute a powerful tool in multimedia forensics. An efficient approach for ENF estimation is introduced with temporal windowing based on the filter-bank Capon spectral estimator. A type of Gohberg-Semencul factorization of the model covariance matrix is used due to the Toeplitz structure of the covariance matrix. Moreover, this approach uses, for the first time in the field of ENF, a temporal window, not necessarily the rectangular one, at the stage preceding spectral estimation.
poster2019.pdf
- Categories:
 27 Views
27 Views
- Categories:
 37 Views
37 Views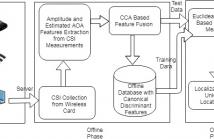
- Read more about FuseLoc: A CCA Based Information Fusion for Indoor Localization Using CSI Phase and Amplitude of WiFi Signals
- Log in to post comments
With the growth of location based services, indoor localization is attracting great interests as it facilitates further ubiquitous environments. In this paper, we propose FuseLoc, the first information fusion based indoor localization using multiple features extracted from Channel State Information (CSI). In FuseLoc, the localization problem is modelled as a pattern matching problem, where the location of a subject is predicted based on the similarity measure of the CSI features of the unknown location with those of the training locations.
- Categories:
 33 Views
33 Views
- Read more about Clonability of anti-counterfeiting printable graphical codes: a machine learning approach
- Log in to post comments
2019_ICASSP.pdf
- Categories:
 16 Views
16 Views
- Read more about Phylogenetic Analysis of Software Using Cache Miss Statistics
- Log in to post comments
While the phylogenetic analysis of multimedia documents keeps being investigated, some recent studies have shown the possibility of re-using the same strategies to analyze the evolution of computer programs (Software Phylogeny), considering its several applications spanning from copyright enforcement to malware detection.
- Categories:
 31 Views
31 Views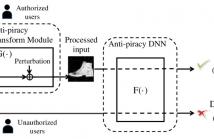
- Read more about Protect Your Deep Neural Networks from Piracy
- Log in to post comments
Building an effective DNN model requires massive human-labeled training data, powerful computing hardware and researchers' skills and efforts. Successful DNN models are becoming important intellectual properties for the model owners and should be protected from unauthorized access and piracy. This paper proposes a novel framework to provide access control to the trained deep neural networks so that only authorized users can utilize them properly.
- Categories:
 77 Views
77 Views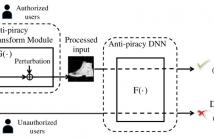
- Read more about Protect Your Deep Neural Networks from Piracy
- Log in to post comments
Building an effective DNN model requires massive human-labeled training data, powerful computing hardware and researchers' skills and efforts. Successful DNN models are becoming important intellectual properties for the model owners and should be protected from unauthorized access and piracy. This paper proposes a novel framework to provide access control to the trained deep neural networks so that only authorized users can utilize them properly.
- Categories:
 20 Views
20 Views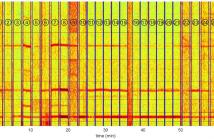
- Read more about Factors Affecting ENF Capture in Audio
- Log in to post comments
The electric network frequency (ENF) signal is an environmental signature that can be captured in audiovisual recordings made in locations where there is electrical activity. This signal is influenced by the power grid in which the recording is made, and recent work has shown that it can be useful toward a number of forensics and security applications. An under-studied area of ENF research is the factors that can affect the capture of ENF traces in media recordings.
- Categories:
 122 Views
122 Views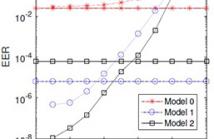
- Read more about Enhanced Geometric Reflection Models for Paper Surface Based Authentication
- Log in to post comments
Paper under the microscopic view has a rough surface formed by intertwisted wood fibers. Such roughness is unique on a specific location of the paper and is almost impossible to duplicate. Previous work has shown that commodity scanners and cameras are capable of capturing such intrinsic roughness in term of surface normal vectors for security and forensics applications. In this paper, we examine several candidate mathematical models for camera captured images of paper surfaces and compare the modeling accuracies with reference to the measurement by the confocal microscopy.
- Categories:
 67 Views
67 Views
- Read more about Security in the Internet of Things: Information Theoretic Insights
- Log in to post comments
The emerging Internet of Things (IoT) has several salient characteristics that differentiate it from existing wireless networking architectures. These include the deployment of very large numbers of (possibly) low-complexity terminals; the need for low-latency, short-packet communications (e.g., to support automation); light or no infrastructure; and primary applications of data gathering, inference and control.
- Categories:
 39 Views
39 Views