
- Read more about Watermarking images in self-supervised latent-spaces - poster
- Log in to post comments
- Categories:
 6 Views
6 Views
- Read more about Watermarking images in self-supervised latent-spaces - slides
- Log in to post comments
- Categories:
 9 Views
9 Views
Deep neural network (DNN) watermarking is one of the main techniques to protect the DNN. Although various DNN watermarking schemes have been proposed, none of them is able to resist the DNN encryption. In this paper, we propose an encryption resistent DNN watermarking scheme, which is able to resist the parameter shuffling based DNN encryption. Unlike the existing schemes which use the kernels separately for watermarking embedding, we propose to embed the watermark into the fused kernels to resist the parameter shuffling.
- Categories:
 11 Views
11 Views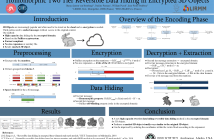
- Read more about Homomorphic Two Tier Reversible Data Hiding in Encrypted 3D Objects
- Log in to post comments
Today, 3D objects are an increasingly popular form of media. It has become necessary to secure them during their transmission or archiving. In this paper, we propose a two tier reversible data hiding method for 3D objects in the encrypted domain. Based on the homomorphic properties of the Paillier cryptosystem, our proposed method embeds a first tier message in the encrypted domain which can be extracted in either the encrypted domain or the clear domain. Indeed, our method produces a marked 3D object which is visually very similar to the original object.
- Categories:
 36 Views
36 Views
- Read more about Extending the Reverse JPEG Compatibility Attack to Double Compressed Images
- Log in to post comments
- Categories:
 5 Views
5 Views
- Read more about IMAGE STEGANOGRAPHY BASED ON ITERATIVE ADVERSARIAL PERTURBATIONS ONTO A SYNCHRONIZED-DIRECTIONS SUB-IMAGE
- Log in to post comments
Nowadays a steganography has to face challenges to both feature-based staganalysis and convolutional neural network (CNN) based steganalysis. In this paper, we present a novel steganographic scheme to incorporate synchronizing modification directions and iterative adversarial perturbations to enhance steganographic performance. Firstly an existing steganographic function is employed to compute initial costs. Then the secret message bits are embedded following clustering modification directions profile.
- Categories:
 12 Views
12 Views
- Read more about Enhancing Image Steganography via Stego Generation and Selection
- Log in to post comments
Unlike most existing steganography methods which are main- ly focused on designing embedding cost, in this paper, we propose a new method to enhance existing steganographic methods via stego generation and selection. The proposed method firstly trains a steganalytic network according to the steganography to be enhanced, and then tries to adjust a tiny part of original embedding costs based on the magnitudes of it and the corresponding gradients obtained from the pre-trained network, and generates many candidate stegos in a random manner.
v-final.pdf
- Categories:
 45 Views
45 Views
- Read more about Fundamental Limits Of Steganographic Capacity For Multivariate-Quantized-Gaussian-Distributed Multimedia
- Log in to post comments
Steganography is the art and science of hiding data within innocent-looking objects (cover objects). Multimedia objects such as images and videos are an attractive type of cover objects due to their high embedding rates. There exist many techniques for performing steganography in both the literature and the practical world. Meanwhile, the definition of the steganographic capacity for multimedia and how to be calculated has not taken full attention.
- Categories:
 36 Views
36 Views
- Read more about Approaching Optimal Embedding in Audio Steganography with GAN
- Log in to post comments
Audio steganography is a technology that embeds messages into audio without raising any suspicion from hearing it. Current steganography methods are based on heuristic cost designs. In this work, we proposed a framework based on Generative Adversarial Network (GAN) to approach optimal embedding for audio steganography in the temporal domain. This is the first attempt to approach optimal embedding with GAN and automatically learn the embedding probability/cost for audio steganography.
- Categories:
 151 Views
151 Views
- Read more about Steganography and its Detection in JPEG Images Obtained with the “Trunc” Quantizer
- Log in to post comments
Many portable imaging devices use the operation of “trunc” (rounding towards zero) instead of rounding as the final quantizer for computing DCT coefficients during JPEG compression. We show that this has rather profound consequences for steganography and its detection. In particular, side-informed steganography needs to be redesigned due to the different nature of the rounding error. The steganographic algorithm J-UNIWARD becomes vulnerable to steganalysis with the JPEG rich model and needs to be adjusted for this source.
- Categories:
 24 Views
24 Views