
- Read more about OPTIMAL DATA TASK DISTRIBUTION FOR BALANCING ENERGY CONSUMPTION ON COOPERATIVE FOG NETWORKS
- Log in to post comments
In this paper, the problem of how to balance the energy consumption during data processing in networks is investigated using a fog middleware. We first demonstrate that for a fog network with different kind of nodes, balancing the energy relies on a combinatorial optimization that is solved using graph theory. We propose a transformation of the transshipment graph problem to formulate an optimization problem that we solve with linear programming (LP).
- Categories:
 9 Views
9 Views
- Read more about Dynamic power Allocation for Smart Grids via ADMM
- Log in to post comments
spawc2018.pdf
- Categories:
 14 Views
14 Views
- Read more about Trade-offs in Data-Driven False Data Injection Attacks Against the Power Grid
- Log in to post comments
We address the problem of constructing false data injection (FDI) attacks that can bypass the bad data detector (BDD) of a power grid. The attacker is assumed to have access to only power flow measurement data traces (collected over a limited period of time) and no other prior knowledge about the grid. Existing related algorithms are formulated under the assumption that the attacker has access to measurements collected over a long (asymptotically infinite) time period, which may not be realistic.
- Categories:
 15 Views
15 Views
- Read more about Chance Constrained Optimization of Distributed Energy Resources via Affine Policies
- Log in to post comments
- Categories:
 12 Views
12 Views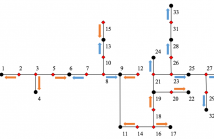
- Read more about Using Smart Meter and PMU Data for Load Inference
- Log in to post comments
Power distribution system operators require knowledge of power injections for accomplishing various grid dispatch tasks. Monitoring, collecting, and processing smart meter data across all grid nodes, however, may not be affordable given the communication and storage resources. In this context,
- Categories:
 69 Views
69 Views- Read more about DELAY AWARE MEASUREMENTS GATHERING IN WAMS COMMUNICATION NETWORK
- Log in to post comments
The rapid deployment of phasor measurements units (PMUs) supporting Wide Area Measurement System (WAMS) in smart grid has opened opportunities to enhance the grid operations through the introduction of WAMS applications. However, the increased deployment of synchrophasor technologies increases the effective attack surface available to attackers and exposesWAMS applications. Such applications have strict and stringent delay requirements, e.g., end to end delay as well as delay variation between measurements from different PMUs.
WAMS_2.pdf
- Categories:
 4 Views
4 Views
- Read more about A Game-Theoretic Approach for Communication-Free Voltage-VAR Optimization
- Log in to post comments
- Categories:
 13 Views
13 Views- Read more about Dynamic ADMM For Real-Time Optimal Power Flow
- Log in to post comments
This paper considers distribution networks featuring distributed energy resources (DERs), and develops a dynamic optimization method to maximize given operational objectives in real time while adhering to relevant network constraints. The design of the dynamic algorithm is based on suitable linearization of the AC power flow equations, and it leverages the
- Categories:
 21 Views
21 Views- Read more about INCORPORATING TIME-OF-DAY USAGE PATTERNS INTO NON-INTRUSIVE LOAD MONITORING
- Log in to post comments
Load monitoring techniques determine the appliances that are turned ON within a given period of time in a household or workplace. They can help occupants optimize their
power consumption behavior. Load monitoring is broadly classified as intrusive or nonintrusive. Intrusive load monitoring requires the attachment of individual sensors to each
- Categories:
 22 Views
22 Views- Read more about Autonomous Navigation of UAV in Large-scale Unknown Complex Environment with Deep Reinforcement Learning
- Log in to post comments
- Categories:
 51 Views
51 Views