
- Read more about How Secure Is the Time-Modulated Array-Enabled OFDM Directional Modulation?
- 1 comment
- Log in to post comments
Time-modulated arrays (TMA) transmitting orthogonal frequency division multiplexing (OFDM) waveforms achieve physical layer security by allowing the signal to reach the legitimate destination undistorted, while making the signal appear scrambled in all other directions. In this paper, we examine how secure the TMA OFDM system is, and show that it is possible for the eavesdropper to defy the scrambling.
- Categories:
 29 Views
29 Views
- Read more about CRYPTO-MINE: Cryptanalysis via Mutual Information Neural Estimation
- Log in to post comments
The use of Mutual Information (MI) as a measure to evaluate the efficiency of cryptosystems has an extensive history. However, estimating MI between unknown random variables in a high-dimensional space is challenging. Recent advances in machine learning have enabled progress in estimating MI using neural networks. This work presents a novel application of MI estimation in the field of cryptography. We propose applying this methodology directly to estimate the MI between plaintext and ciphertext in a chosen plaintext attack.
CryptoMine.pdf
- Categories:
 22 Views
22 Views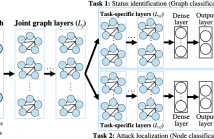
- Read more about A Graph Neural Network Multi-Task Learning-Based Approach for Detection and Localization of Cyberattacks in Smart Grids
- Log in to post comments
False data injection attacks (FDIAs) on smart power grids' measurement data present a threat to system stability. When malicious entities launch cyberattacks to manipulate the measurement data, different grid components will be affected, which leads to failures. For effective attack mitigation, two tasks are required: determining the status of the system (normal operation/under attack) and localizing the attacked bus/power substation. Existing mitigation techniques carry out these tasks separately and offer limited detection performance.
- Categories:
 62 Views
62 Views
- Categories:
 38 Views
38 Views
- Read more about Improved Probabilistic Context-free Grammars for Passwords Using Word Extraction
- Log in to post comments
Probabilistic context-free grammars (PCFGs) have been proposed to capture password distributions, and further been used in password guessing attacks and password strength meters. However, current PCFGs suffer from the limitation of inaccurate segmentation of password, which leads to misestimation of password probability and thus seriously affects their performance. In this paper, we propose a word extraction approach for passwords, and further present an improved PCFG model, called WordPCFG.
- Categories:
 15 Views
15 Views
- Read more about Application-Layer DDoS Attacks with Multiple Emulation Dictionaries
- Log in to post comments
We consider the problem of identifying the members of a botnet under an application-layer (L7) DDoS attack, where a target site is flooded with a large number of requests that emulate legitimate users’ patterns. This challenging problem has been recently addressed with reference to two simplified scenarios, where either all bots pick requests from the same emulation dictionary (total overlap), or they are divided in separate clusters corresponding to distinct emulation dictionaries (no overlap at all).
icassp_slides.pdf
- Categories:
 54 Views
54 Views

- Read more about Key Agreement and Secure Identification with Physical Unclonable Functions (PUFs)
- Log in to post comments
- Categories:
 53 Views
53 Views
- Read more about Hybrid Precoding for Secure Transmission in Reflect-Array-Assisted Massive MIMO Systems
- Log in to post comments
Recently, a hybrid analog-digital architecture has been proposed for multiuser MIMO transmission in the millimeter-wave spectrum using reflect-arrays. The architecture exhibits scalability and high energy-efficiency while keeping the transmitter cost-efficient. Inspired by this architecture, we design a secure multiuser hybrid analog-digital precoding scheme. This scheme utilizes the method of regularized least-squares to shape the downlink beamformers, such that the signal received via malicious terminals is effectively suppressed.
- Categories:
 108 Views
108 Views
- Read more about Low-complexity and Reliable Transforms for Physical Unclonable Functions
- Log in to post comments
Noisy measurements of a physical unclonable function (PUF) are used to store secret keys with reliability, security, privacy, and complexity constraints. A new set of low-complexity and orthogonal transforms with no multiplication is proposed to obtain bit-error probability results significantly better than all methods previously proposed for key binding with PUFs. The uniqueness and security performance of a transform selected from the proposed set is shown to be close to optimal.
- Categories:
 27 Views
27 Views