- Read more about TWO-DIMENTIONAL ANTI-JAMMING COMMUNICATION BASED ON DEEP REINFORCEMENT LEARNING
- Log in to post comments
- Categories:
 8 Views
8 Views
- Read more about Asymptotic Perfect Secrecy in Distributed Estimation for Large Sensor Networks
- Log in to post comments
This paper considers asymptotic perfect secrecy and asymptotic perfect estimation in distributed estimation for large sensor networks under threat of an eavesdropper, which has access to all sensor outputs. To measure secrecy, we compare the estimation performance at the fusion center and at eavesdropper in terms of their respective Fisher Information. We analyze the Fisher Information ratio between the fusion center and eavesdropper and derive the maximum achievable ratio when the channels between sensors and eavesdropper are noisy binary symmetric channels.
- Categories:
 2 Views
2 Views
- Read more about Reliable Secret-key Binding for Physical Unclonable Functions with Transform Coding
- Log in to post comments
Different transforms are compared to extract bit sequences used in secret-key binding for highly-correlated physical-identifier outputs. A set of transforms that perform well in terms of decorrelation efficiency is applied to ring oscillator (RO) outputs to improve the reliability and uniqueness of the extracted sequence, information leakage to an eavesdropper about the secret key and RO outputs, secret-key length, and hardware cost.
- Categories:
 12 Views
12 Views
- Read more about Achieving Semantic Security Without Keys Through Coding And All-Or-Nothing Transforms Over Wireless Channels
- Log in to post comments
We propose a simple protocol which allows two legitimate parties to exchange some confidential message over a wireless
channel with some chosen level of semantic security against passive eavesdroppers, and without needing either secret or public keys. The proposed method leverages the noisy and fading nature of the channel and exploits coding and all-or-nothing transforms to achieve the desired level of semantic security. We also define suitable metrics to estimate the semantic security level in the considered setting.
- Categories:
 Views
Views
- Read more about PHYSICAL LAYER SECURITY GAME WITH FULL-DUPLEX PROACTIVE EAVESDROPPER
- Log in to post comments
- Categories:
 8 Views
8 Views- Read more about HONEY CHATTING: A NOVEL INSTANT MESSAGING SYSTEM ROBUST TO EAVESDROPPING OVER COMMUNICATION
- Log in to post comments
- Categories:
 11 Views
11 Views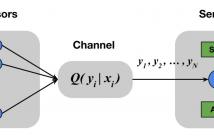
This is an overview poster on designing a privacy-preserving randomized requantization scheme which simultaneously guarantees local differential privacy and reduces bit-rate of input signals.
For more information, please check out the publication at IEEE Xplore:
S. Xiong, A.D. Sarwate, and N.B. Mandayam, “Randomized requantization with local differential privacy,” in Proceedings of the 41st International Conference on Acoustics, Speech and Signal Processing, March 2016.
- Categories:
 6 Views
6 Views
This is an overview poster on designing a privacy-preserving randomized requantization scheme which simultaneously guarantees local differential privacy and reduces bit-rate of input signals.
For more information, please check out the publication at IEEE Xplore:
S. Xiong, A.D. Sarwate, and N.B. Mandayam, “Randomized requantization with local differential privacy,” in Proceedings of the 41st International Conference on Acoustics, Speech and Signal Processing, March 2016.
ICASSP2016.pdf
- Categories:
 11 Views
11 Views
This is an overview poster on designing a privacy-preserving randomized requantization scheme which simultaneously guarantees local differential privacy and reduces bit-rate of input signals.
For more information, please check out the publication at IEEE Xplore:
S. Xiong, A.D. Sarwate, and N.B. Mandayam, “Randomized requantization with local differential privacy,” in Proceedings of the 41st International Conference on Acoustics, Speech and Signal Processing, March 2016.
ICASSP2016.pdf
- Categories:
 12 Views
12 Views