
- Read more about On Covert Communication Over Infinite-Bandwidth Gaussian Channels
- Log in to post comments
- Categories:
 13 Views
13 Views
- Read more about Mutual-Information-Private Online Gradient Descent Algorithm
- Log in to post comments
A user implemented privacy preservation mechanism is proposed for the online gradient descent (OGD) algorithm. Privacy is measured through the information leakage as quantified by the mutual information between the usersʼ outputs and learnerʼs inputs. The input perturbation mechanism proposed can be implemented by individual users with a space and time complexity that is independent of the horizon T. For the proposed mechanism, the information leakage is shown to be bounded by the Gaussian channel capacity in the full information setting.
newfile5.pdf
- Categories:
 30 Views
30 Views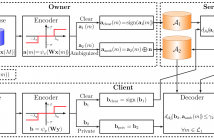
- Read more about Privacy-Preserving Outsourced Media Search Using Secure Sparse Ternary Codes
- Log in to post comments
In this paper, we propose a privacy-preserving framework for outsourced media search applications. Considering three parties, a data owner, clients and a server, the data owner outsources the description of his data to an external server, which provides a search service to clients on the behalf of the data owner. The proposed framework is based on a sparsifying transform with ambiguization, which consists of a trained linear map, an element-wise nonlinearity and a privacy amplification.
- Categories:
 9 Views
9 Views- Read more about On the Indistinguishability of Compressed Encryption With Partial Unitary Sensing Matrices
- Log in to post comments
- Categories:
 13 Views
13 Views- Read more about Visual Saliency-Based Confidentiality Metric for Selective Crypto-Compressed JPEG Images
- Log in to post comments
For security reasons, more and more digital data are transferred or stored in encrypted domains. In particular for images, selective format-compliant JPEG encryption methods have been proposed for the last ten years. Since encryption is selective, in order to reduce the processing time and to be format-compliant, it is now necessary to evaluate the confidentiality of these selective crypto-compressed JPEG images. It is known that image quality metrics, such as PSNR or SSIM, give a very low correlation with a mean opinion score (MOS) for low quality images.
- Categories:
 11 Views
11 Views- Read more about Secure Genomic Susceptibility Testing based on Lattice Encryption
- Log in to post comments
Recent advances in Next Generation Sequencing have increased the availability of genomic data for more accurate analyses, like testing for the genetic susceptibility to a disease. Current laboratories' facilities cannot cope with this data growth, and genomic processing needs to be outsourced, comprising serious privacy risks.
- Categories:
 24 Views
24 Views- Categories:
 6 Views
6 Views- Categories:
 5 Views
5 Views- Categories:
 6 Views
6 Views