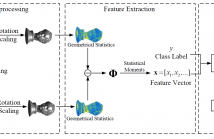
3D steganalysis aims to find the changes embedded through steganographic or information hiding algorithms into 3D models. This research study proposes to use new 3D features, such as the edge vectors, represented in both Cartesian and Laplacian coordinate systems, together with other steganalytic features, for improving the results of 3D steganalysers. In this way the local feature vector used by the steganalyzer is extended to 124 dimensions.
- Categories:
 16 Views
16 Views
- Read more about A New Joint Watermarking-Encryption-JPEG-LS Compression Method for a Priori & a Posteriori Image Protection_Poster
- Log in to post comments
In this paper, we propose the first joint watermarking-encryption-compression scheme for the protection of medical images. Its originality is twofold. In a first time, it allows the access to watermarking-based security services from the encrypted and the compressed bitstreams without having to parse them even partially. It becomes possible to trace images and control their reliability (i.e. integrity and authenticity) from both the encrypted and compressed domains.
- Categories:
 48 Views
48 Views
- Read more about Watermarking and rank metric codes
- Log in to post comments
This paper presents a different way to improve the resistance of digital watermarking. Using the well known Lattice QIM in the spatial domain, we analyze the interest of using a different kind of error correcting codes: rank metric codes. These codes are already used in communications for network coding but not used in the context of watermarking. In this article, we show how this metric permits to correct errors with a specific structure and is adapted to specific image attacks. We propose a first study to validate the concept of rank metric for watermarking process.
- Categories:
 22 Views
22 Views
- Read more about Yedrouj-Net: An efficient CNN for spatial steganalysis Results Conclusions • An efficient approach based on deep learning (CNN) for steganalysis. • Our method outperforms the state-of-the-art and others CNN-based models with and without taking extra measu
- Log in to post comments
For about 10 years, detecting the presence of a secret message hidden
in an image was performed with an Ensemble Classifier trained
with Rich features. In recent years, studies such as Xu et al. have
indicated that well-designed Convolutional Neural Networks(CNN)
can achieve comparable performance to the two-step machine learning
approaches.
In this paper we propose a CNN that outperforms the state-ofthe-
art in terms of error probability. The proposition is in the continuity
of what has been recently proposed and it is a clever fusion
- Categories:
 14 Views
14 ViewsThe QR (Quick Response) code is a two-dimensional barcode, which was designed for storage information and high speed reading applications. Being cheap to produce and fast to read, it becomes actually a popular solution for product labeling.
Ones try to make QR code a solution against counterfeiting. We present a novel technique that permits to create a secure printed QR code which is robust
- Categories:
 616 Views
616 Views- Read more about A NEW BLIND COLOR IMAGE WATERMARKING BASED ON A PSYCHOVISUAL MODEL AND QUANTIZATION APPROACHES
- Log in to post comments
- Categories:
 8 Views
8 Views- Read more about RETHINKING THE HIGH CAPACITY 3D STEGANOGRAPHY: INCREASING ITS RESISTANCE TO STEGANALYSIS
- Log in to post comments
3D steganography is used in order to embed or hide information into 3D objects without causing visible or machine detectable modifications. In this paper we rethink about a high capacity 3D steganography based on the Hamiltonian path quantization, and increase its resistance to steganalysis. We analyze the parameters that may influence the distortion of a 3D shape as well as the resistance of the steganography to 3D steganalysis. According to the experimental results, the proposed high capacity 3D steganographic method has an increased resistance to steganalysis.
- Categories:
 4 Views
4 Views- Read more about STEGANOGRAPHY WITH TWO JPEGS OF THE SAME SCENE
- Log in to post comments
- Categories:
 3 Views
3 Views- Read more about Benchmarking of Scoring Functions for Bias-Based Fingerprinting Code
- Log in to post comments
icassp16.pdf
- Categories:
 9 Views
9 Views
- Read more about Checking Up the Health of Multimedia Security
- Log in to post comments
The terminology "multimedia security" gained a new popularity in the mid-90s with the rapid rise of digital watermarking in an attempt to combat piracy of copyrighted content. This milestone incarnates the mutation of content protection techniques from conventional cryptography to signal processing techniques. Today, multimedia security encompasses a much wider range of techniques such as multimedia encryption, content fingerprinting, anti-camcording, passive forensic analysis.
- Categories:
 3 Views
3 Views