
Lecture notes for undergraduate and first-year graduate students on digital watermarking and data embedding in multimedia data.
Based on lectures developed at University of Maryland, College Park, USA.
- Categories:
 230 Views
230 Views
- Read more about MaskMark: Robust Neural Watermarking for Real and Synthetic Speech (Slides)
- 1 comment
- Log in to post comments
High-quality speech synthesis models may be used to spread misinformation or impersonate voices. Audio watermarking can help combat such misuses by embedding a traceable signature in generated audio. However, existing audio watermarks are not designed for synthetic speech and typically demonstrate robustness to only a small set of transformations of the watermarked audio. To address this, we propose MaskMark, a neural network-based digital audio watermarking technique optimized for speech.
- Categories:
 98 Views
98 Views
The widespread adoption of smartphones has introduced new challenges to document copyright protection, prompting the emergence of Screen-Shooting Resilient Document Watermarking (SSRDW) technology. In recent years, underpainting-based SSRDW techniques have proven to be highly effective. However, after careful study, we find that existing methods fail to simultaneously meet four essential criteria for SSRDW: high imperceptibility, strong
- Categories:
 24 Views
24 Views
- Read more about ADAPTIVE VIDEO WATERMARKING WITH PERCEPTUAL GUARANTEE AND EFFICIENCY OPTIMIZATION
- Log in to post comments
Existing video watermarking embeds robust watermarks in each frame of the video for copyright protection and tracking. However, just as any content written on a blank paper is easily perceived, embedding watermarks in the texture-poor frames impairs imperceptibility. Common geometric attacks such as scaling and rotation pose a significant challenge to the existing video watermarking. Image watermarking based on moments is robust against geometric attacks.
- Categories:
 35 Views
35 Views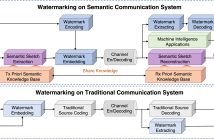
- Read more about SEMANTIC SECURITY: A DIGITAL WATERMARK METHOD FOR IMAGE SEMANTIC PRESERVATION
- Log in to post comments
This is a poster on a proposed watermarking method. In the research, we first chose position vector domain instead of traditional spatial or frequency domain. In addition, we successfully implemented watermarking on semantic communication system. Third, we modeled watermarking channel so that researchers could systematically research watermarking process.
For more information, please check out the publication at IEEE Xplore:
- Categories:
 31 Views
31 Views
- Read more about EXPLORING CONSISTENT SPATIO-TEMPORAL DISTORTION AND STABLE 3-D DCT COEFFICIENTS FOR ROBUST BLIND VIDEO WATERMARKING
- Log in to post comments
With the rapid development of mobile Internet and video applications, robust video watermarking technology has become a focal area of research for protecting and tracking intellectual property rights in digital media. An important characteristic of video is that it has both spatial and temporal properties. Previous studies in video watermarking have primarily focused on either spatial or temporal distortions and did not uniformly consider all types of video distortion, which restricts the robustness of video watermarking.
- Categories:
 26 Views
26 Views
- Read more about A study on the invariance in security whatever the dimension of images for the steganalysis by deep-learning
- Log in to post comments
In this paper, we study the performance invariance of convolutional neural networks when confronted with variable image sizes in the context of a more ”wild steganalysis”. First, we propose two algorithms and definitions for a fine experimental protocol with datasets owning ”similar difficulty” and ”similar security”. The ”smart crop 2” algorithm allows the introduction of the Nearly Nested Image Datasets (NNID) that ensure ”a similar difficulty” between various datasets, and a dichotomous research algorithm allows a ”similar security”.
- Categories:
 17 Views
17 Views
- Read more about Mixer: DNN Watermarking using Image Mixup
- Log in to post comments
It is crucial to protect the intellectual property rights of DNN models prior to their deployment. The
DNN should perform two main tasks: its primary task and watermarking task. This paper proposes
a lightweight, reliable, and secure DNN watermarking that attempts to establish strong ties between
these two tasks. The samples triggering the watermarking task are generated using image Mixup
either from training or testing samples. This means that there is an infinity of triggers not limited to the
- Categories:
 13 Views
13 Views
Generative models are now capable of synthesizing images, speeches, and videos that are hardly distinguishable from authentic contents. Such capabilities cause concerns such as malicious impersonation and IP theft. This paper investigates a solution for model attribution, i.e., the classification of synthetic contents by their source models via watermarks embedded in the contents.
- Categories:
 111 Views
111 ViewsSteganography comprises the mechanics of hiding data in a host media that may be publicly available. While previous works focused on unimodal setups (e.g., hiding images in images, or hiding audio in audio), PixInWav targets the multimodal case of hiding images in audio. To this end, we propose a novel residual architecture operating on top of short-time discrete cosine transform (STDCT) audio spectrograms. Among our results, we find that the residual steganography setup we propose allows an encoding of the hidden image that is independent from the host audio without compromising quality.
- Categories:
 130 Views
130 Views