- Watermarking and Steganography
- Signal Processing and Cryptography
- Multimedia Forensics
- Communications and Network Security
- Biometrics
- Applications

- Read more about SEMI-SUPERVISED FEATURE EMBEDDING FOR DATA SANITIZATION IN REAL-WORLD EVENTS
- Log in to post comments
With the rapid growth of data sharing through social media networks, determining relevant data items concerning a particular subject becomes paramount. We address the issue of establishing which images represent an event of interest through a semi-supervised learning technique. The method learns consistent and shared features related to an event (from a small set of examples) to propagate them to an unlabeled set. We investigate the behavior of five image feature representations considering low- and high-level features and their combinations.
slides_icassp2021.pdf
- Categories:
 24 Views
24 Views
- Read more about Secure Identification for Gaussian Channels
- Log in to post comments
New applications in modern communications are demanding robust and ultra-reliable low latency information exchange such as machine-to-machine and human-to-machine communications. For many of these applications, the identification approach of Ahlswede and Dueck is much more efficient than the classical transmission scheme proposed by Shannon. Previous studies concentrate mainly on identification over discrete channels. We focus on Gaussian channels for their known practical relevance. We deal with secure identification over Gaussian channels.
- Categories:
 19 Views
19 Views
- Read more about Secure Identification for Gaussian Channels
- Log in to post comments
New applications in modern communications are demanding robust and ultra-reliable low latency information exchange such as machine-to-machine and human-to-machine communications. For many of these applications, the identification approach of Ahlswede and Dueck is much more efficient than the classical transmission scheme proposed by Shannon. Previous studies concentrate mainly on identification over discrete channels. We focus on Gaussian channels for their known practical relevance. We deal with secure identification over Gaussian channels.
- Categories:
 59 Views
59 Views
- Read more about Efficient Capon-based approach exploiting temporal windowing for electric network frequency estimation
- Log in to post comments
Electric Network Frequency (ENF) fluctuations constitute a powerful tool in multimedia forensics. An efficient approach for ENF estimation is introduced with temporal windowing based on the filter-bank Capon spectral estimator. A type of Gohberg-Semencul factorization of the model covariance matrix is used due to the Toeplitz structure of the covariance matrix. Moreover, this approach uses, for the first time in the field of ENF, a temporal window, not necessarily the rectangular one, at the stage preceding spectral estimation.
poster2019.pdf
- Categories:
 28 Views
28 Views
- Categories:
 47 Views
47 Views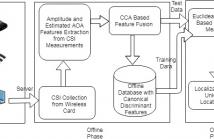
- Read more about FuseLoc: A CCA Based Information Fusion for Indoor Localization Using CSI Phase and Amplitude of WiFi Signals
- Log in to post comments
With the growth of location based services, indoor localization is attracting great interests as it facilitates further ubiquitous environments. In this paper, we propose FuseLoc, the first information fusion based indoor localization using multiple features extracted from Channel State Information (CSI). In FuseLoc, the localization problem is modelled as a pattern matching problem, where the location of a subject is predicted based on the similarity measure of the CSI features of the unknown location with those of the training locations.
- Categories:
 38 Views
38 Views
- Read more about Clonability of anti-counterfeiting printable graphical codes: a machine learning approach
- Log in to post comments
2019_ICASSP.pdf
- Categories:
 25 Views
25 Views
- Read more about Phylogenetic Analysis of Software Using Cache Miss Statistics
- Log in to post comments
While the phylogenetic analysis of multimedia documents keeps being investigated, some recent studies have shown the possibility of re-using the same strategies to analyze the evolution of computer programs (Software Phylogeny), considering its several applications spanning from copyright enforcement to malware detection.
- Categories:
 41 Views
41 Views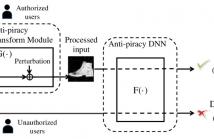
- Read more about Protect Your Deep Neural Networks from Piracy
- Log in to post comments
Building an effective DNN model requires massive human-labeled training data, powerful computing hardware and researchers' skills and efforts. Successful DNN models are becoming important intellectual properties for the model owners and should be protected from unauthorized access and piracy. This paper proposes a novel framework to provide access control to the trained deep neural networks so that only authorized users can utilize them properly.
- Categories:
 85 Views
85 Views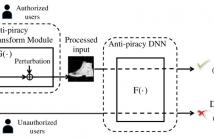
- Read more about Protect Your Deep Neural Networks from Piracy
- Log in to post comments
Building an effective DNN model requires massive human-labeled training data, powerful computing hardware and researchers' skills and efforts. Successful DNN models are becoming important intellectual properties for the model owners and should be protected from unauthorized access and piracy. This paper proposes a novel framework to provide access control to the trained deep neural networks so that only authorized users can utilize them properly.
- Categories:
 34 Views
34 Views