- Watermarking and Steganography
- Signal Processing and Cryptography
- Multimedia Forensics
- Communications and Network Security
- Biometrics
- Applications
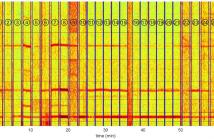
- Read more about Factors Affecting ENF Capture in Audio
- Log in to post comments
The electric network frequency (ENF) signal is an environmental signature that can be captured in audiovisual recordings made in locations where there is electrical activity. This signal is influenced by the power grid in which the recording is made, and recent work has shown that it can be useful toward a number of forensics and security applications. An under-studied area of ENF research is the factors that can affect the capture of ENF traces in media recordings.
- Categories:
 139 Views
139 Views
- Read more about Enhanced Geometric Reflection Models for Paper Surface Based Authentication
- Log in to post comments
Paper under the microscopic view has a rough surface formed by intertwisted wood fibers. Such roughness is unique on a specific location of the paper and is almost impossible to duplicate. Previous work has shown that commodity scanners and cameras are capable of capturing such intrinsic roughness in term of surface normal vectors for security and forensics applications. In this paper, we examine several candidate mathematical models for camera captured images of paper surfaces and compare the modeling accuracies with reference to the measurement by the confocal microscopy.
- Categories:
 85 Views
85 Views
- Read more about Security in the Internet of Things: Information Theoretic Insights
- Log in to post comments
The emerging Internet of Things (IoT) has several salient characteristics that differentiate it from existing wireless networking architectures. These include the deployment of very large numbers of (possibly) low-complexity terminals; the need for low-latency, short-packet communications (e.g., to support automation); light or no infrastructure; and primary applications of data gathering, inference and control.
- Categories:
 42 Views
42 Views
- Read more about REVERSIBLE DATA HIDING IN ENCRYPTED IMAGES BASED ON RESERVING ROOM AFTER ENCRYPTION AND MULTIPLE PREDICTORS
- Log in to post comments
This paper proposes a new vacating room after encryption reversible data hiding scheme. Hidden data is embedded into the encrypted host image by bit-flipping a preselected bitplane of a randomly formed pixel group. The major novelty of the paper is the use of multiple predictors in an adaptive procedure for detecting between original and modified pixels. Four predictors are used on a context of four neighbors, namely the average of the four pixels, a weighted average based on local gradients, the median and the midpoint. Experimental results are provided.
- Categories:
 42 Views
42 Views
- Read more about Making Likelihood Ratios Digestible for Cross-Application Performance Assessment
- Log in to post comments
Performance estimation is crucial to the assessment of novel algorithms and systems. In detection error trade-off (DET) diagrams, discrimination performance is solely assessed targeting one application, where cross-application performance considers risks resulting from decisions, depending on application constraints. For the purpose of interchangeability of research results across different application constraints, we propose to augment DET curves by depicting systems regarding their support of security and convenience levels.
poster.pdf
- Categories:
 70 Views
70 Views- Read more about Keynote: Physical Security is from Mars, Cybersecurity is from Venus
- Log in to post comments
Corporations are dealing with the traditions of managing security in silos, leading to an increased number of attacks on things like critical infrastructure. Corporate (Physical) Security deals with facilities and building access, whereas IT Security is dealing with cybersecurity as well as system and network access. It’s as if they are living on different planets!
- Categories:
 42 Views
42 Views
- Read more about Discriminant Correlation Analysis for Feature Level Fusion with Application to Multimodal Biometrics
- Log in to post comments
In this paper, we present Discriminant Correlation Analysis (DCA), a feature level fusion technique that incorporates the class associations in correlation analysis of the feature sets. DCA performs an effective feature fusion by maximizing the pair-wise correlations across the two feature sets, and at the same time, eliminating the between-class correlations and restricting the correlations to be within classes.
- Categories:
 120 Views
120 Views
- Categories:
 2 Views
2 Views
- Read more about Full-duplex vs. Half-duplex Secret-key Generation
- Log in to post comments
- Categories:
 41 Views
41 Views