- Watermarking and Steganography
- Signal Processing and Cryptography
- Multimedia Forensics
- Communications and Network Security
- Biometrics
- Applications

- Read more about Single Relay Selection for Secure Communication in a Cooperative System with Multiple Full-Duplex DnF Relays
- Log in to post comments
- Categories:
 8 Views
8 Views- Read more about Towards Resilient Cyber-Physical Control Systems
- Log in to post comments
- Categories:
 5 Views
5 Views
- Read more about Article Summaries - SPM Special Issue on Signal Processing for Art Investigation
- Log in to post comments
Expanded version of the Guest Editorial
for Special Issue on Signal Processing for Art Investigation
(IEEE Signal Processing Magazine, July 2015)
Include short summaries for each of the 11 articles in the special issue.
- Categories:
 15 Views
15 Views
Abstract—While personal data privacy is threatened by online
social networks, researchers are seeking for privacy protection
tools and methods to assist online social network providers
and users. In this paper, we aim to address this problem by
investigating how to quantitatively evaluate the privacy risk, as
a function of people’s awareness of privacy risks as well as
whether their friends can be trusted to protect their personal
data. We present a trust-aware privacy evaluation framework,
- Categories:
 17 Views
17 Views
- Read more about Exploring Compression Effects for Improved Source Camera Identification Using Strongly Compressed Video
- 1 comment
- Log in to post comments
This paper presents a study of the video compression effect on source camera identification based on the Photo-Response Non-Uniformity (PRNU). Specifically, the reliability of different types of frames in a compressed video is first investigated, which shows quantitatively that I-frames are more reliable than P-frames for PRNU estimation. Motivated by this observation, a new mechanism for estimating the reference PRNU and two mechanisms for estimating the test-video PRNU are proposed to achieve higher accuracy with fewer frames used.
- Categories:
 25 Views
25 Views
Yuhong Liu (University of Rhode Island), “Security and Applications of Digital Trust and Reputation” (2012), Advisor: Prof. Yan Lindsay Sun
- Categories:
 45 Views
45 Views
Cyber Competition has been recognized as an efficient way to facilitate research and education in cyber security Cyber Competition has been recognized as an efficient way to facilitate research and education in cyber security field [1]–[3]. We have discovered that the participants (i.e. players) in cyber competitions can cheat in order to gain a higher rank or collect more prizes. In this work, we use data collected from the CANT competition to analyze such cheating behaviors and propose to build a competition social network to detect cheating behaviors in cyber competitions.
- Categories:
 25 Views
25 Views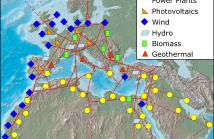
We offer algorithms and visualization techniques for cyber trust in a Smart Grid system. Cyber trust is evaluated in terms of a mathematical model consisting of availability, detection and false alarm trust values, as well as a model of predictability. We develop a prototype Cyber Situational Awareness Visualization (CyberSAVe) tool to visualize cyber trust. We provide Operational Decision Aids (ODAs) displayed in context with a SCADA management information. We define cyber trust metrics, which are calculated and displayed in real-time in the Metric Assessment System (MAS) of CyberSAVe.
- Categories:
 120 Views
120 Views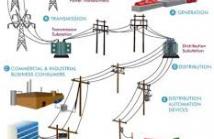
The security issue of complex networks has drawn significant concerns recently. While pure topological analyzes from a network security perspective provide some effective techniques, their inability to characterize the physical principles requires a more comprehensive model to approximate failure behavior of a complex network in reality. In this paper, based on an extended topological metric, we proposed an approach to examine the vulnerability of a specific type of complex network, i.e., the power system, against cascading failure threats.
- Categories:
 136 Views
136 Views
- Read more about Load Distribution Vector Based Attack Strategies against Power Grid Systems (Poster)
Security issues in complex systems such as power grid, communication network, Internet, among others have attracted wide attention from academic, government and industry. In this paper, we investigate the vulnerabilities of power grid under a topology-based network model in the context of cascading failures caused by physical attacks against substations and transmission lines. In particular, we develop attack strategies from the attackers' points of view, aiming to cause severe damage to the network efficiency, as a way to revealing the vulnerability of the system.
- Categories:
 13 Views
13 Views