
- Read more about ADT: ANTI-DEEPFAKE TRANSFORMER
- Log in to post comments
Recently almost all the mainstream deepfake detection methods use Convolutional Neural Networks (CNN) as their backbone. However, due to the overreliance on local texture information, which is usually determined by forgery methods of training data, these CNN based methods cannot generalize well to unseen data. To get out of the predicament of prior methods, in this paper, we propose a novel transformer-based framework to model both global and local information and analyze anomalies of face images.
- Categories:
 22 Views
22 Views
- Read more about FORENSIC ANALYSIS AND LOCALIZATION OF MULTIPLY COMPRESSED MP3 AUDIO USING TRANSFORMERS
- Log in to post comments
Audio signals are often stored and transmitted in compressed formats. Among the many available audio compression schemes, MPEG-1 Audio Layer III (MP3) is very popular and widely used. Since MP3 is lossy it leaves characteristic traces in the compressed audio which can be used forensically to expose the past history of an audio file. In this paper, we consider the scenario of audio signal manipulation done by temporal splicing of compressed and uncompressed audio signals. We propose a method to find the temporal location of the splices based on transformer networks.
icassp_2022_poster.pdf
- Categories:
 16 Views
16 Views
Misleading or false information has been creating chaos in some places around the world. To mitigate this issue, many researchers have proposed automated fact-checking methods to fight the spread of fake news. However, most methods cannot explain the reasoning behind their decisions, failing to build trust between machines and humans using such technology. Trust is essential for fact-checking to be applied in the real world. Here, we address fact-checking explainability through question answering.
- Categories:
 12 Views
12 Views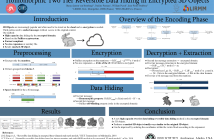
- Read more about Homomorphic Two Tier Reversible Data Hiding in Encrypted 3D Objects
- Log in to post comments
Today, 3D objects are an increasingly popular form of media. It has become necessary to secure them during their transmission or archiving. In this paper, we propose a two tier reversible data hiding method for 3D objects in the encrypted domain. Based on the homomorphic properties of the Paillier cryptosystem, our proposed method embeds a first tier message in the encrypted domain which can be extracted in either the encrypted domain or the clear domain. Indeed, our method produces a marked 3D object which is visually very similar to the original object.
- Categories:
 37 Views
37 Views
- Categories:
 11 Views
11 Views
- Categories:
 8 Views
8 Views
- Categories:
 15 Views
15 Views
- Read more about SEMI-SUPERVISED FEATURE EMBEDDING FOR DATA SANITIZATION IN REAL-WORLD EVENTS
- Log in to post comments
With the rapid growth of data sharing through social media networks, determining relevant data items concerning a particular subject becomes paramount. We address the issue of establishing which images represent an event of interest through a semi-supervised learning technique. The method learns consistent and shared features related to an event (from a small set of examples) to propagate them to an unlabeled set. We investigate the behavior of five image feature representations considering low- and high-level features and their combinations.
slides_icassp2021.pdf
- Categories:
 24 Views
24 Views
- Read more about Exposing GAN-generated Faces Using Inconsistent Corneal Specular Highlights
- 1 comment
- Log in to post comments
- Categories:
 35 Views
35 Views
- Read more about Learning to Fool the Speaker Recognition (poster)
- Log in to post comments
Due to the widespread deployment of fingerprint/face/speaker recognition systems, attacking deep learning based biometric systems has drawn more and more attention. Previous research mainly studied the attack to the vision-based system, such as fingerprint and face recognition. While the attack for speaker recognition has not been investigated yet, although it has been widely used in our daily life.
- Categories:
 103 Views
103 Views