- Read more about On the Supermodularity of Active Graph-based Semi-supervised Learning with Stieltjes Matrix Regularization
- Log in to post comments
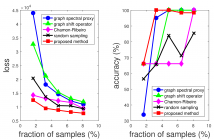
Active graph-based semi-supervised learning (AG-SSL) aims to select a small set of labeled examples and utilize their graph-based relation to other unlabeled examples to aid in machine learning tasks. It is also closely related to the sampling theory in graph signal processing. In this paper, we revisit the original formulation of graph-based SSL and prove the supermodularity of an AG-SSL objective function under a broad class of regularization functions parameterized by Stieltjes matrices.
- Categories:
 83 Views
83 Views
- Read more about THE CHORD GAP DIVERGENCE AND A GENERALIZATION OF THE BHATTACHARYYA DISTANCE
- Log in to post comments
- Categories:
 22 Views
22 Views
- Read more about PARALLEL VECTOR FIELD REGULARIZED NON-NEGATIVE MATRIX FACTORIZATION FOR IMAGE REPRESENTATION
- Log in to post comments
- Categories:
 28 Views
28 Views
- Read more about A Greedy Pursuit Algorithm For Separating Signals From Nonlinear Compressive Observations
- Log in to post comments
In this paper we study the unmixing problem which aims
to separate a set of structured signals from their superposition.
In this paper, we consider the scenario in which
the mixture is observed via nonlinear compressive measurements.
We present a fast, robust, greedy algorithm called
Unmixing Matching Pursuit (UnmixMP) to solve this problem.
We prove rigorously that the algorithm can recover the
constituents from their noisy nonlinear compressive measurements
with arbitrarily small error. We compare our algorithm
- Categories:
 6 Views
6 Views
- Read more about AN IMPROVED INITIALIZATION FOR LOW-RANK MATRIX COMPLETION BASED ON RANK-1 UPDATES
- Log in to post comments
Given a data matrix with partially observed entries, the low-rank matrix completion problem is one of finding a matrix with the lowest rank that perfectly fits the given observations. While there exist convex relaxations for the low-rank completion problem, the underlying problem is inherently non-convex, and most algorithms (alternating projection, Riemannian optimization, etc.) heavily depend on the initialization. This paper proposes an improved initialization that relies on successive rank-1 updates.
- Categories:
 32 Views
32 Views
- Read more about Improved Algorithms for Differentially private Orthogonal Tensor Decomposition
- Log in to post comments
Tensor decompositions have applications in many areas including signal processing, machine learning, computer vision and neuroscience. In this paper, we propose two new differentially private algorithms for orthogonal decomposition of symmetric tensors from private or sensitive data; these arise in applications such as latent variable models. Differential privacy is a formal privacy framework that guarantees protections against adversarial inference.
- Categories:
 19 Views
19 Views
- Read more about Differentially private Distributed Principal Component Analysis
- Log in to post comments
Differential privacy is a cryptographically-motivated formal privacy definition that is robust against strong adversaries. The principal component analysis (PCA) algorithm is frequently used in signal processing, machine learning, and statistics pipelines. In many scenarios, private or sensitive data is distributed across different sites: in this paper we propose a differentially private distributed PCA scheme to enable collaborative dimensionality reduction.
- Categories:
 39 Views
39 Views
- Categories:
 7 Views
7 ViewsIn this paper, we propose a differentially-private canonical correlation analysis algorithm. Canonical correlation analysis (CCA) is often used in clustering applications for multi-view data. CCA finds subspaces for each view such that projecting each of the views onto these subspaces simultaneously reduces the dimension and maximizes correlation. Differential-privacy is a framework for understanding the risk of inferring the data input to the algorithm based on the output.
- Categories:
 32 Views
32 Views- Read more about ONLINE CONVOLUTIONAL DICTIONARY LEARNING
- Log in to post comments
While a number of different algorithms have recently been proposed for convolutional dictionary learning, this remains an expensive problem. The single biggest impediment to learning from large training sets is the memory requirements, which grow at least linearly with the size of the training set since all existing methods are batch algorithms. The work reported here addresses this limitation by extending online dictionary learning ideas to the convolutional context.
- Categories:
 11 Views
11 Views