
- Read more about Continuous Security In IoT Using Blockchain
- Log in to post comments
The two major roadblocks for state of the art Internet of Things (IoT) infrastructure like smart buildings, smart cities, etc. are lack of trust between various entities of system and single point of failure which is a vulnerability causing extreme damage to the whole system. This paper proposes a blockchain based IoT security solution where, trust is established through the immutable and decentralized nature of blockchain. The distributed nature of blockchain makes the system more robust and immune to single point of failure.
- Categories:
 57 Views
57 Views
- Read more about DIGITALSEAL: A Transaction Authentication Tool for Online and Offline Transactions
- Log in to post comments
We introduce DigitalSeal, a transaction authentication tool that works in both online and offline use scenarios. DigitalSeal is a digital scanner that reads transaction information sent by an issuing entity of the DigitalSeal reader for authentication, and the information is encoded using a specially crafted bar-code. DigitalSeal views various pieces of transaction information for users to verify and proceed with transaction authentication. DigitalSeal is generic, and is capable of reading information viewed on paper, computer monitors (similarly, kiosk monitors), and mobile phones.
- Categories:
 18 Views
18 Views
- Read more about Optimal Online Cyberbullying Detection
- Log in to post comments
Cyberbullying has emerged as a serious societal and public health problem that demands accurate methods for the detection of cyberbullying instances in an effort to mitigate the consequences. While techniques to automatically detect cyberbullying incidents have been developed, the scalability and timeliness of existing cyberbullying detection approaches have largely been ignored. We address this gap by formulating cyberbullying detection as a sequential hypothesis testing problem. Based on this formulation, we propose a novel
- Categories:
 30 Views
30 Views- Read more about ROBUST IMAGE IDENTIFICATION WITH SECURE FEATURES FOR JPEG IMAGES
- Log in to post comments
PID2499.pdf
- Categories:
 8 Views
8 Views- Read more about ALIGNED DISCRIMINATIVE POSE ROBUST DESCRIPTORS FOR FACE AND OBJECT RECOGNITION
- Log in to post comments
Face and object recognition in uncontrolled scenarios due to pose and illumination variations, low resolution, etc. is a challenging research area. Here we propose a novel descriptor, Aligned Discriminative Pose Robust ( ADPR) descriptor, for matching faces and objects across pose which is also robust to resolution and illumination variations. We generate virtual intermediate pose subspaces from training examples at a few poses and compute the alignment matrices of those subspaces with the frontal subspace.
- Categories:
 3 Views
3 Views
- Read more about Discriminant Correlation Analysis for Feature Level Fusion with Application to Multimodal Biometrics
- Log in to post comments
In this paper, we present Discriminant Correlation Analysis (DCA), a feature level fusion technique that incorporates the class associations in correlation analysis of the feature sets. DCA performs an effective feature fusion by maximizing the pair-wise correlations across the two feature sets, and at the same time, eliminating the between-class correlations and restricting the correlations to be within classes.
- Categories:
 120 Views
120 Views- Read more about Detection of False Data Injection Attacks in Smart Grid Communication Systems
- Log in to post comments
The transformation of traditional energy networks to smart grids can assist in revolutionizing the energy industry in terms of reliability, performance and manageability. However, increased connectivity of power grid assets for bidirectional communications presents severe security vulnerabilities. In this paper, we investigate Chi-square detector and cosine similarity matching approaches for attack detection in smart grids where Kalman filter estimation is used to measure any deviation from actual measurements.
- Categories:
 7 Views
7 Views- Categories:
 12 Views
12 Views
We propose a simple yet effective method for visualizing and classifying malware using image processing techniques. Malware binaries are visualized as gray-scale images, with the observation that for many malware families, the images belonging to the same family appear very similar in layout and texture. Motivated by this visual similarity, a classification method using standard image features is proposed. Neither disassembly nor code execution is required for classification.
- Categories:
 131 Views
131 Views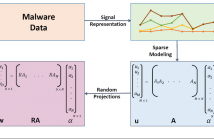
- Read more about SATTVA: SpArsiTy inspired classificaTion of malware VAriants
- Log in to post comments
There is an alarming increase in the amount of malware that is generated today. However, several studies have shown that most of these new malware are just variants of existing ones. Fast detection of these variants plays an effective role in thwarting new attacks. In this paper, we propose a novel approach to detect malware variants using a sparse representation framework. Exploiting the fact that most malware variants have small differences in their structure, we model a new/unknown malware sample as a sparse linear combination of other malware in the training set.
- Categories:
 6 Views
6 Views