
ICASSP is the world’s largest and most comprehensive technical conference focused on signal processing and its applications. The ICASSP 2020 conference will feature world-class presentations by internationally renowned speakers, cutting-edge session topics and provide a fantastic opportunity to network with like-minded professionals from around the world. Visit website.
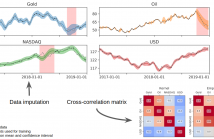
In Financial Signal Processing, multiple time series such as financial indicators, stock prices and exchange rates are strongly coupled due to their dependence on the latent state of the market and therefore they are required to be jointly analysed. We focus on learning the relationships among financial time series by modelling them through a multi-output Gaussian process (MOGP) with expressive covariance functions. Learning these market dependencies among financial series is crucial for the imputation and prediction of financial observations.
- Categories:
 19 Views
19 Views
- Read more about An ensemble Based Approach for Generalized Detection of Spoofing Attacks to Automatic Speaker Recognizers
- Log in to post comments
As automatic speaker recognizer systems become mainstream, voice spoofing attacks are on the rise. Common attack strategies include replay, the use of text-to-speech synthesis, and voice conversion systems. While previously-proposed end-to-end detection frameworks have shown to be effective in spotting attacks for one particular spoofing strategy, they have relied on different models, architectures, and speech representations, depending on the spoofing strategy.
- Categories:
 34 Views
34 Views
- Read more about STRUCTURAL SPARSIFICATION FOR FAR-FIELD SPEAKER RECOGNITION WITH INTEL GNA
- Log in to post comments
- Categories:
 74 Views
74 Views
The problem of maximizing the information flow through a sensor network tasked with an inference objective at the fusion center is considered. The sensor nodes take observations, compress, and send them to the fusion center through a network of relays. The network imposes capacity constraints on the rate of transmission in each connection and flow conservation constraints. It is shown that this rate-constrained inference problem can be cast as a Network Utility Maximization problem by suitably defining the utility functions for each sensor, and can be solved using existing techniques.
- Categories:
 14 Views
14 Views
Banding artifact, or false contouring, is a common video compression impairment that tends to appear on large flat regions in encoded videos. These staircase-shaped color bands can be very noticeable in high-definition videos. Here we study this artifact, and propose a new distortion-specific no-reference video quality model for predicting banding artifacts, called the Blind BANding Detector (BBAND index). BBAND is inspired by human visual models. The proposed detector can generate a pixel-wise banding visibility map and output a banding severity score at both the frame and video levels.
- Categories:
 23 Views
23 Views
- Read more about Meta Learning for Robust Child/Adult Classification from Speech
- Log in to post comments
Computational modeling of naturalistic conversations in clinical applications has seen growing interest in the past decade. An important use-case involves child-adult interactions within the autism diagnosis and intervention domain. In this paper, we address a specific sub-problem of speaker diarization, namely child-adult speaker classification in such dyadic conversations with specified roles. Training a speaker classification system robust to speaker and channel conditions is challenging due to inherent variability in the speech within children and the adult interlocutors.
- Categories:
 85 Views
85 Views
- Read more about STOCHASTIC GEOMETRY PLANNING OF ELECTRIC VEHICLES CHARGING STATIONS
- Log in to post comments
Smart grids are faced with the challenge of meeting the ever increasing load demands of electric vehicles (EVs). To provide acceptable charging services, operators need to be equipped with an efficient charging stations (CSs) planning strategy. Unfortunately, existing planning solutions are quite limited. They normally rely on standard IEEE bus systems or power grids that are specific to certain cities. In this paper, using stochastic geometry, we formulate the CSs planning on a stochastic geometry-based power grid model, that we previously showed to mimic real-world power grids.
- Categories:
 42 Views
42 Views
- Read more about Steganography and its Detection in JPEG Images Obtained with the “Trunc” Quantizer
- Log in to post comments
Many portable imaging devices use the operation of “trunc” (rounding towards zero) instead of rounding as the final quantizer for computing DCT coefficients during JPEG compression. We show that this has rather profound consequences for steganography and its detection. In particular, side-informed steganography needs to be redesigned due to the different nature of the rounding error. The steganographic algorithm J-UNIWARD becomes vulnerable to steganalysis with the JPEG rich model and needs to be adjusted for this source.
- Categories:
 28 Views
28 Views
- Read more about Online Graph Topology Inference with Kernels for Brain Connectivity Estimation - ICASSP 2020 slides
- Log in to post comments
- Categories:
 12 Views
12 Views
- Categories:
 23 Views
23 Views